Write up SHX 3 (PHP Security) - Quantum Photos
This is another Write Up of SHX 3 from Shellter Labs, continuing with the theme Security with PHP
Problem description:
“We know that flag is in the source code. Can you read it?”
It also offer a link to the site to be explored, and when you access the site, we see this:
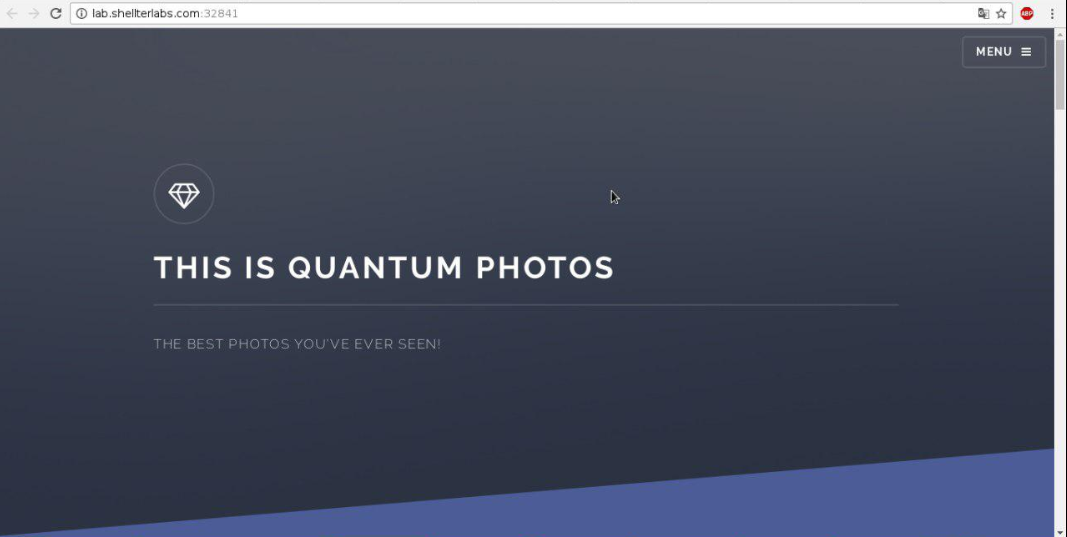
Solution
When I selected one of the menu pages, I saw the url is in this format: http://lab.shellterlabs.com:32841/index.php?page=home.html and I soon realized that this is a very common vulnerability in Web applications in PHP, which is LFI (Local File Inclusion). To make sure it was an LFI flaw, I tried to include the Linux /etc/passwd file (and Unix in general), which is where the operating system stores the information about each of the users that can enter the system, to include I changed the url for http://lab.shellterlabs.com:32841/index.php?page=../../../etc/passwd and the entire contents of the passwd file was shown in screen.
Apesar de saber qual a vulnerabilidade da página, ainda não temos o que importa, que é flag, e como a descrição do problema diz que a flag está no código fonte, mas se incluirmos o arquivo index.php na página através de http://lab.shellterlabs.com:32841/index.php?page=index.php ainda não teremos o código php da página, pois este será incluído e interpretado (e provavelmente entrará em loop infinito de inclusão de arquivo).
So, to get access to the source code we can use a php wrapper that allows us to access the code. This way:
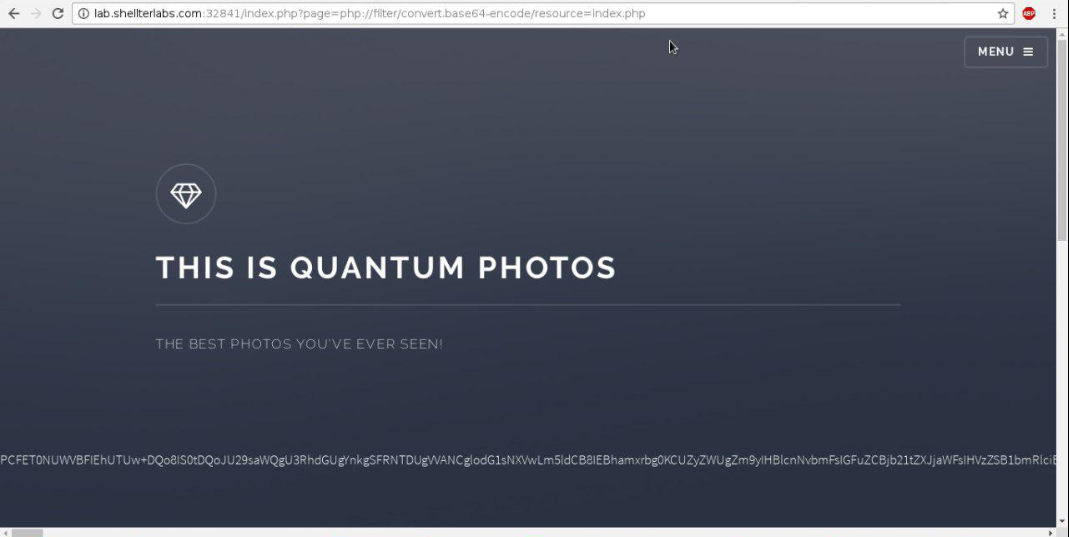
After that, when decoding the code in base64, it is possible to see and flag in the source code.
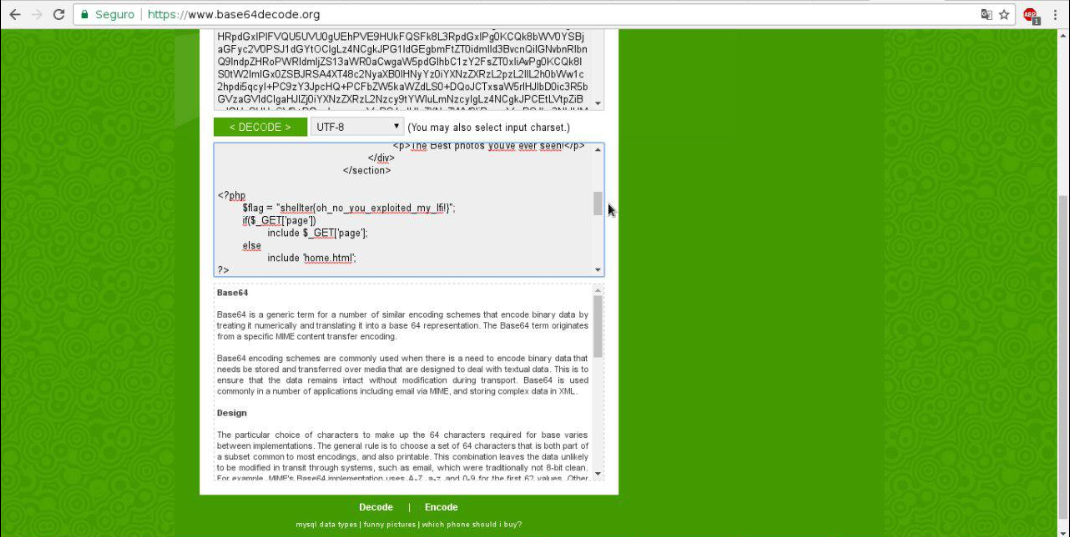
Moral of the story: Never include files directly from user inputs.